My score
On the CB 2021 Practice MCQ, I got a 49/70, but only attempted 54 questions, meaning out of the ones I completed, spending about a minute on every question, I got a 49/54.
Corrections
Q1 : Phishing
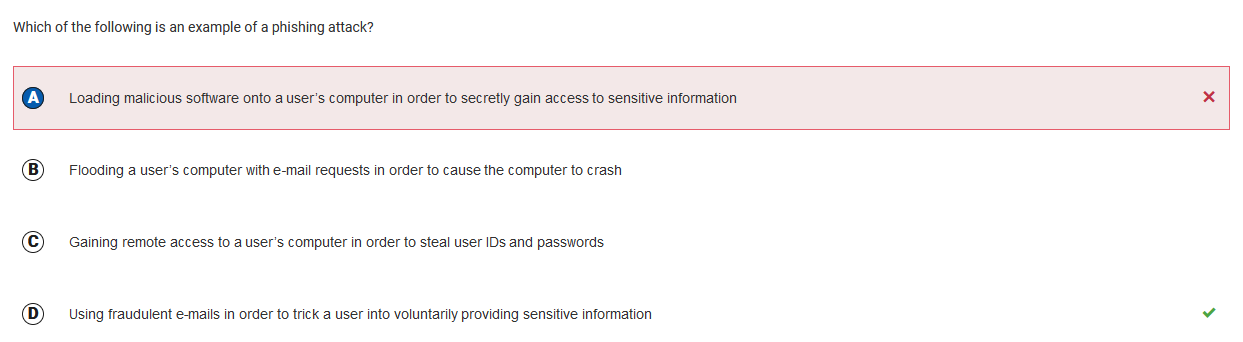
My answer was incorrect. Phishing is to pose as someone other than yourself, usually someone that would trust the victim. Then, you send them a file, or something to download that would steal their information, or convince them to give up their information. Knowing this information, D is the correct answer, as the fraudulent user would be the one disguising themself trying to get information from their victim.
Q27 : Bias
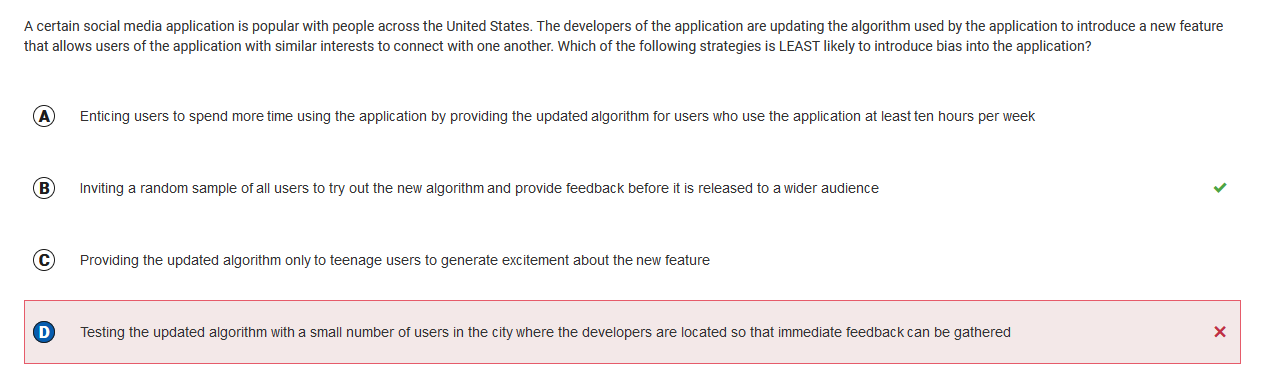
In my answer, “random” people are chosen, but they are only chosen in the city where the developers are, creating bias. To have less bias, the developers could choose random people out of everywhere on their platform, not just where they are. Knowing this, B would be the correct answer, because completely random users are chosen out of those who use the platform.
Q30 : Data Transmission
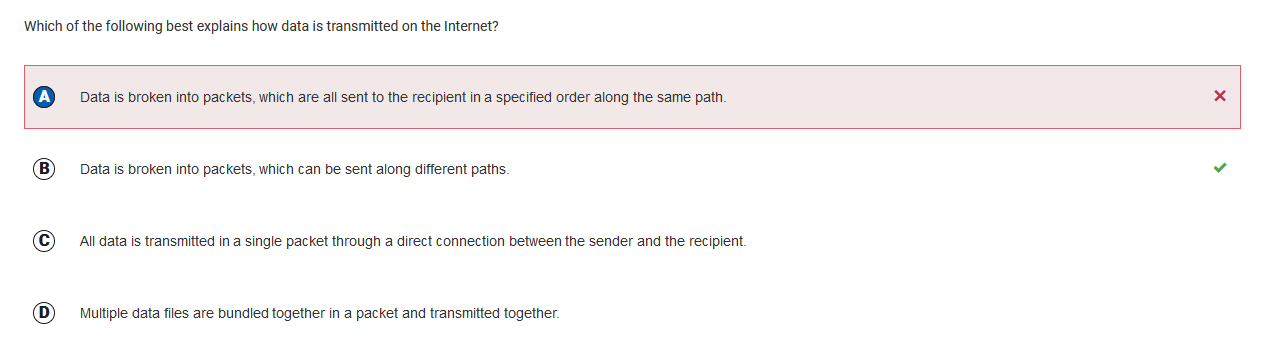
While data is broken into packets to be transmissed, they aren’t always sent in a specific way. B, the correct answer, is a better answer, as it more generally decines how data is transmissed.
Q33 : Algorithms
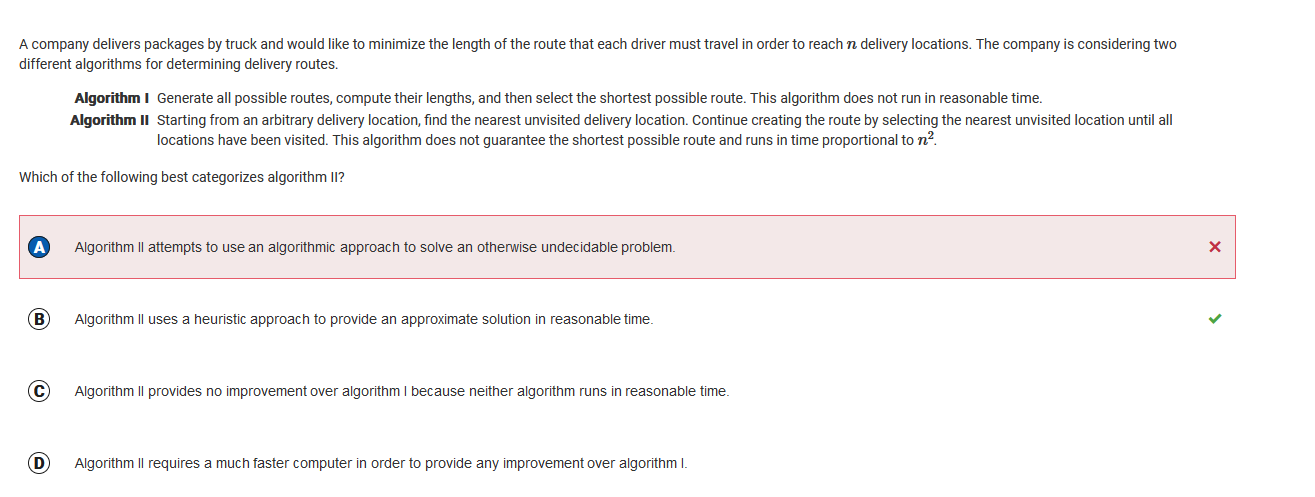
I got this question wrong because of a lack of vocabulary. I didn’t understand the meaning of heuristic, but now knowing that the definition is a technique designed to make problem solving faster, I can see that B is correct, becuase algorithm II does problem solving to calculate delivery locations and routes.
Q52 : Binary Search
I got this question wrong because I didn’t understand the difference between linear and binary searching. If a list has 128 elements, in a linear search, all of them can be accessed, but in a binary search, only 8 at a time can be accessed while searching.
Popcorn Hacks
Format:
Question
My answer 5tttrrt55555555555555
555555555t5tr
CB Explanation
4. Cause of Overflow
In a certain computer program, two positive integers are added together, resulting in an overflow error. Which of the following best explains why the error occurs?
C: The precision of the result is limited due to the constraints of using a floating-point representation.
Overflow errors occur when an arithmetic operation results in a value outside the range of numbers that can be represented by a fixed number of bits.
5. Logic Circuit
The diagram below shows a circuit composed of three logic gates. Each gate takes two inputs and produces a single output. For which of the following input values will the circuit have an output of true ?
C: A = false, B = true, C = true, D = true
With these inputs, the OR gate will produce an output of true and the first AND gate will produce an output of true. Since both inputs to the second AND gate will be true, the circuit will have an output of true.
11. Color in Binary Triplet
A color in a computing application is represented by an RGB triplet that describes the amount of red, green, and blue, respectively, used to create the desired color. A selection of colors and their corresponding RGB triplets are shown in the following table. Each value is represented in decimal (base 10). According to information in the table, what color is represented by the binary RGB triplet (11111111, 11111111, 11110000) ?
A: Ivory
The binary number 11111111 is equal to 255. The binary number 11110000 is equal to , or 240. Therefore, the given binary triplet represents the color ivory.
15. Output Comparison
Which of the following best compares the values displayed by programs A and B?
A: Program A and program B display identical values in the same order.
23. Flowchart
C: Available <– weekday AND miles >= 20
The algorithm in the flowchart requires both conditions to be true in order to set available to true.
50. Reasonable Time
Consider the following algorithms. Each algorithm operates on a list containing n elements, where n is a very large integer.
An algorithm that accesses each element in the list twice
An algorithm that accesses each element in the list n times
An algorithm that accesses only the first 10 elements in the list, regardless of the size of the list
Which of the algorithms run in reasonable time?
B: III Only
Algorithm I accesses elements 2n times (twice for each of n elements), which is considered reasonable time. Algorithm II accesses n^2 elements (n times for each of n elements), which is considered reB:asonable time.
56. Execution Times
An online game collects data about each player’s performance in the game. A program is used to analyze the data to make predictions about how players will perform in a new version of the game.
The procedure GetPrediction (idNum) returns a predicted score for the player with ID number idNum. Assume that all predicted scores are positive. The GetPrediction procedure takes approximately 1 minute to return a result. All other operations happen nearly instantaneously.
Two versions of the program are shown below.
D: Version II requires approximately 5 more minutes to execute than version I.
Version I calls the GetPrediction procedure once for each element of idList, or four times total. Since each call requires 1 minute of execution time, version I requires approximately 4 minutes to execute. Version II calls the GetPrediction procedure twice for each element of idList, and then again in the final display statement. This results in the procedure being called nine times, requiring approximately 9 minutes of execution time.
64. Multiplication Error
The following procedure is intended to return the value of x times y, where x and y are integers. Multiplication is implemented using repeated additions.
For which of the following procedure calls does the procedure NOT return the intended value?
B: Multilpy 2, -5 and D: Multiply -2, -5
Since y is initially negative, the loop condition count ≥ y is initially true, so the body of the loop is never executed and 0 is returned.
65. Concatenating
Which of the following can be used to store the string “jackalope” in the string variable animal ?
Select two answers.
B:
animal
Substring (“antelope”, 5, 4)
animal
Concat (“a”, animal)
animal Concat (Substring (“jackrabbit”, 1, 4), animal)
and C:
animal
Substring (“jackrabbit”, 1, 4)
animal
Concat (animal, “a”)
animal Concat (animal, Substring (“antelope”, 5, 4))
This code segment stores the substring “lope” in animal. It then concatenates “a” and “lope”, storing the result “alope” in animal. Lastly, it concatenates the substring “jack” and “alope”, storing the result “jackalope” in animal.
67. Procedure Errors
The procedure NumOccurrences is intended to count and return the number of times targetWord appears in the list wordList. The procedure does not work as intended.
For which of the following code segments will the call to NumOccurrences NOT return the intended value?
Select two answers.
A: treeList <- “birch”, “maple”, “birch” numOccurences treelist, “birch”
B: treeList <- “birch”, “maple”, “oak” numOccurences treelist, “maple”
For this code segment, count is increased to 1 the first time “birch” is encountered in the list. However, count is reset to 0 when the code segment moves to the next list element. The last time “birch” is encountered in the list, count is again increased to 1, causing the procedure to return 1 instead of the intended result 2.